Have you ever wondered how your online messages stay private? Symmetric encryption plays a crucial role in protecting sensitive information, ensuring that only authorized parties can access it. This powerful method uses the same key for both encryption and decryption, making it efficient and fast for various applications.
What Is Symmetric Encryption?
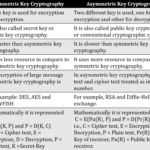
Symmetric encryption employs a single key for both encryption and decryption processes. This method ensures that the same key used to lock the information is also required to unlock it, making it crucial for secure communications.
Common examples of symmetric encryption algorithms include:
- AES (Advanced Encryption Standard): Widely adopted due to its strength and efficiency.
- DES (Data Encryption Standard): An older standard, less common today due to vulnerabilities.
- 3DES (Triple DES): An enhancement of DES that applies the algorithm three times for added security.
- RC4: A stream cipher known for its speed, though it has fallen out of favor due to weaknesses.
You’ll find symmetric encryption in various applications, such as securing emails or protecting files. It’s essential in VPNs (Virtual Private Networks), ensuring safe data transmission over public networks.
- Speed: Faster than asymmetric methods due to simpler computations.
- Efficiency: Works well with large amounts of data.
- Simplicity: The process involves straightforward key management compared to more complex systems.
While symmetric encryption offers robust protection, key management remains vital. If someone gains access to your secret key, they can decrypt your sensitive information easily. Hence, using strong keys and proper storage solutions is critical.
Key Characteristics of Symmetric Encryption
Symmetric encryption relies on a single secret key for both encrypting and decrypting data. This method has several key characteristics that contribute to its effectiveness in securing information.
Shared Secrets
Shared secrets are central to symmetric encryption. Both the sender and receiver must possess the same key, ensuring secure communication. If unauthorized individuals access this key, they can decrypt messages easily. Examples of shared secret scenarios include:
- Secure email exchanges: When two parties communicate securely via encrypted emails.
- File protection: Storing sensitive documents with a password known only to authorized users.
- VPN connections: Establishing secure tunnels over public networks by sharing keys between users and servers.
Speed and Efficiency
Speed and efficiency distinguish symmetric encryption from other methods. It processes large amounts of data quickly due to its straightforward algorithmic structure. For instance:
- AES (Advanced Encryption Standard) performs rapid encryption for bulk data transfers.
- DES (Data Encryption Standard), while outdated, demonstrates how speed enhances user experience in older systems.
You’ll find that these algorithms are designed for high performance, making them ideal for real-time applications like video conferencing or online transactions.
Common Algorithms Used
Several algorithms play a crucial role in symmetric encryption, providing robust security for sensitive information. Each algorithm has unique features and use cases that enhance data protection.
AES (Advanced Encryption Standard)
AES is one of the most widely used symmetric encryption algorithms. It’s known for its speed and security, making it suitable for a variety of applications. AES supports key sizes of 128, 192, and 256 bits, allowing flexibility based on security needs. Organizations often utilize AES to encrypt files, secure communications over the internet, and protect sensitive data in databases.
DES (Data Encryption Standard)
<strong.DES was once the standard for symmetric encryption but is now considered outdated. It uses a fixed key size of 56 bits, which makes it vulnerable to modern attacks. While still relevant in some legacy systems, it’s generally replaced by more secure options like AES. However, understanding DES remains important as it laid the groundwork for later developments in cryptography.
Applications of Symmetric Encryption
Symmetric encryption plays a vital role in various applications aimed at protecting sensitive information. Understanding these applications helps you grasp the significance of this method in today’s digital landscape.
Data Protection
Data protection is crucial for maintaining confidentiality. You often encounter symmetric encryption in securing files and databases. For instance, organizations use AES to encrypt sensitive customer data stored on servers. Similarly, many cloud storage services implement symmetric encryption to safeguard user files from unauthorized access. This ensures that even if a breach occurs, the stolen data remains unreadable without the appropriate key.
Secure Communication
Secure communication relies heavily on symmetric encryption methods. Messaging apps frequently utilize symmetric algorithms to protect user conversations. For example, WhatsApp employs end-to-end encryption using AES to ensure that only intended recipients can read messages. Additionally, VPNs (Virtual Private Networks) use symmetric encryption protocols like IPsec to secure internet traffic between devices and servers, providing privacy while browsing online.
Advantages and Disadvantages
Symmetric encryption offers significant benefits while also presenting some challenges. Understanding these aspects ensures better implementation and usage.
Benefits of Symmetric Encryption
Speed is a key advantage of symmetric encryption. Algorithms like AES process data quickly, making them ideal for real-time applications. Efficiency with large data volumes enhances its usability. For instance, organizations encrypt extensive databases without noticeable slowdowns. Simpler key management contributes to its appeal. With only one key to handle, it reduces complexity compared to asymmetric methods.
Limitations to Consider
Key distribution poses a challenge in symmetric encryption. If the shared secret gets compromised, unauthorized individuals can decrypt sensitive information. Lack of scalability can hinder larger systems. As the number of users increases, managing keys becomes cumbersome. The reliance on strong keys is crucial. Weak or poorly stored keys may lead to security breaches, emphasizing the importance of robust key management practices.