Have you ever wondered how hackers gain access to your sensitive information? Password cracking is a technique that exposes the vulnerabilities in our digital security. It involves methods used to guess or recover passwords from data that’s been stored or transmitted. As cyber threats become more sophisticated, understanding this concept becomes crucial for safeguarding your personal and professional data.
In this article, you’ll explore various examples of password cracking techniques like brute force attacks and dictionary attacks. You’ll learn how these methods work and why they pose a significant risk to your online accounts. By grasping the mechanics behind password cracking, you can better protect yourself against potential breaches. So are you ready to dive deeper into the world of cybersecurity and discover how to fortify your defenses?
What Is Password Cracking?
Password cracking refers to the methods used to gain unauthorized access to accounts by deciphering passwords. This technique exploits weaknesses in digital security, making it essential to understand its implications. Here are some common examples of password cracking methods:
- Brute Force Attack: This method involves trying every possible combination of characters until the password is found. It can take a long time but often succeeds if passwords are weak.
- Dictionary Attack: Instead of random combinations, this approach uses a list of commonly used passwords and variations. Many people use simple words or phrases, making dictionary attacks effective.
- Rainbow Table Attack: Hackers use precomputed tables containing hashed passwords and their corresponding plaintext values. If they find a match, they can quickly crack the password without trial and error.
- Social Engineering: Sometimes attackers bypass technical means altogether. They trick individuals into revealing their passwords through phishing emails or fake websites.
Understanding these techniques helps you recognize potential vulnerabilities in your own security practices. By adopting stronger password policies and using two-factor authentication, you significantly reduce the risk of falling victim to these tactics.
Methods of Password Cracking
Understanding the various methods of password cracking is essential for protecting your accounts. Each technique has unique characteristics and risks associated with it.
Brute Force Attack
A brute force attack involves trying every possible combination of characters until the correct password is found. This method can be effective, especially against weak passwords. For example, if a password consists of only four digits (0000 to 9999), it takes minimal time to crack. However, as password complexity increases—say eight characters including letters and symbols—the time required expands exponentially.
Dictionary Attack
A dictionary attack utilizes a list of commonly used words or phrases to guess passwords. Hackers exploit the tendency for individuals to select simple or predictable passwords. For instance, many users might choose “password123” or “letmein.” This approach speeds up the process compared to random guessing because it starts with likely possibilities.
Social Engineering
Social engineering bypasses technical barriers by manipulating people into revealing their passwords. Phishing emails often trick users into clicking malicious links that appear legitimate. For example, an email masquerading as a bank alert may ask you to log in through a fake website. Once you enter your credentials, hackers gain immediate access without needing any complex algorithms.
By being aware of these methods, you can take proactive steps toward securing your accounts and minimizing vulnerabilities.
Tools Used in Password Cracking
Password cracking relies on various tools that help hackers exploit weaknesses in digital security. Understanding these tools can enhance your awareness of potential risks.
Popular Software
Several software programs are frequently used for password cracking. These include:
- John the Ripper: This open-source tool supports multiple platforms and cracks passwords through brute force and dictionary attacks. Its flexibility makes it a popular choice among security professionals.
- Hashcat: Known for its speed, Hashcat handles different hash algorithms efficiently. It’s designed to run on GPUs, making it capable of tackling complex passwords quickly.
- Cain & Abel: This Windows-based tool specializes in recovering passwords from various sources like network traffic and cached files. It combines several techniques, including brute force, dictionary attacks, and cryptanalysis.
These software options provide hackers with powerful capabilities to compromise accounts if not adequately protected.
Online Services
There are also online services dedicated to password cracking. Some notable examples include:
- CrackStation: A web-based service that uses a massive database of hashed passwords to identify weak ones quickly.
- OnlineHashCrack: This platform allows users to submit hashes for cracking by leveraging cloud computing resources while offering both free and paid services.
- Have I Been Pwned?: While not a direct cracking service, this site lets you check if your email has been compromised in data breaches. Awareness helps you strengthen your password choices moving forward.
By recognizing these tools and services, you can take proactive steps to safeguard your accounts against potential threats associated with password cracking techniques.
Consequences of Password Cracking
Password cracking can lead to severe repercussions for both individuals and organizations. Understanding these consequences helps you recognize the importance of robust security measures.
Impact on Individuals
Password cracking affects individuals by compromising personal data. When hackers gain access, they can exploit sensitive information such as social security numbers, financial details, or private communications.
- Identity Theft: Hackers may impersonate you to open bank accounts or make purchases.
- Financial Loss: Unauthorized transactions can drain your bank account without warning.
- Emotional Distress: The violation of privacy often leads to anxiety and stress.
You might think that using complex passwords mitigates risks, but many people still fall victim due to other vulnerabilities like phishing scams.
Impact on Organizations
Organizations face significant challenges when password cracking occurs. A successful attack can harm reputation and lead to financial losses.
- Data Breaches: Compromised databases expose customer information, resulting in legal liabilities.
- Operational Disruption: Cyberattacks may force companies to halt operations for remediation efforts.
- Loss of Trust: Customers lose confidence in brands that fail to protect their data adequately.
Moreover, businesses must invest heavily in cybersecurity measures post-breach. This includes employee training and upgrading technology systems. You might wonder if these investments are worth it—consider the potential fallout from a breach versus the cost of prevention; the latter is often far less damaging.
Prevention Strategies
Preventing password cracking requires implementing effective security measures. Focus on the following strategies to enhance your account protection.
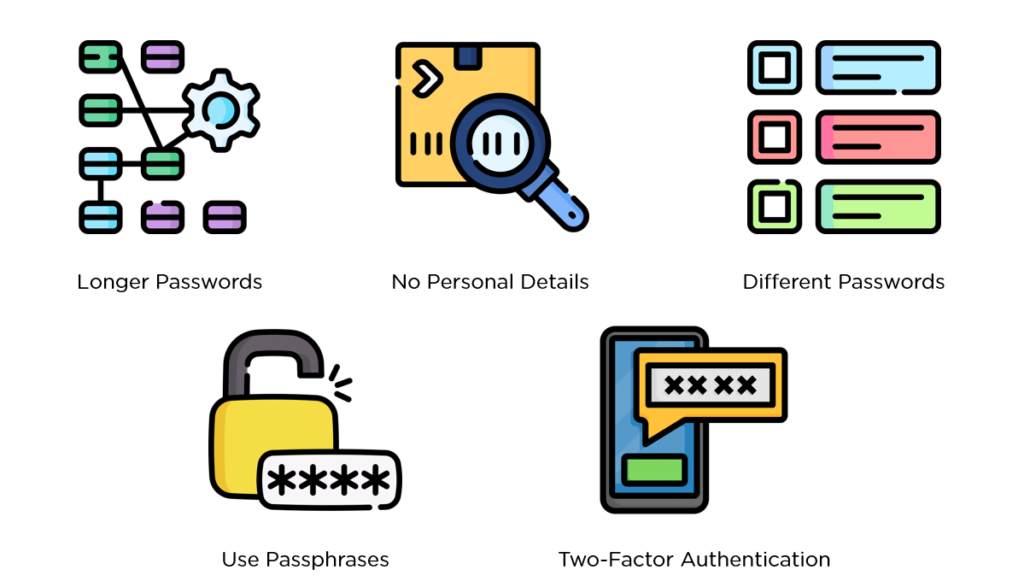
Strong Password Practices
Utilize complex passwords that combine letters, numbers, and symbols. For example, instead of using “password123,” opt for something like “P@55w0rd!2025.” This complexity makes it harder for hackers to guess your password through brute force attacks. Additionally, consider changing your passwords regularly and avoid reusing them across different accounts.
Employ a password manager to store and generate unique passwords securely. These tools can create strong passwords automatically, taking the burden off you while ensuring high security. Remember that even with strong passwords, sharing them or writing them down can lead to vulnerabilities.
Multi-Factor Authentication
Enable multi-factor authentication (MFA) wherever possible. MFA adds an extra layer of security by requiring not only a password but also another form of verification—like a code sent to your phone or an authentication app. This means that even if someone cracks your password, they still can’t access your account without the second factor.
Select authenticator apps over SMS-based codes if available. While SMS is convenient, it’s potentially more vulnerable to interception. Apps like Google Authenticator or Authy provide better security because they generate time-sensitive codes directly on your device.
By integrating these prevention strategies into your routine, you significantly reduce the risks associated with password cracking and protect sensitive information more effectively.