In today’s digital landscape, security is more crucial than ever. Have you ever wondered how to protect your online accounts from unauthorized access? Two factor authentication (2FA) examples offer powerful solutions that can significantly enhance your account security. By requiring two forms of verification, 2FA adds an extra layer of protection against cyber threats.
Overview of Two Factor Authentication
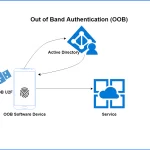
Two-factor authentication (2FA) adds a crucial layer of security to your online accounts. It requires two distinct forms of verification, which significantly decreases the risk of unauthorized access. Here are some common examples:
- SMS Verification: After entering your password, you receive a text message with a one-time code on your mobile device. You enter this code to gain access.
- Authenticator Apps: Apps like Google Authenticator generate time-sensitive codes that you input after your password. This method doesn’t rely on SMS and is often more secure.
- Email Verification: A confirmation link or code sent to your registered email can verify your identity after logging in.
- Hardware Tokens: Devices such as YubiKey provide physical tokens that must be inserted or tapped during the login process.
Each example enhances security by ensuring that even if someone steals your password, they cannot access your account without the second form of verification. Implementing 2FA significantly improves protection from cyber threats and data breaches.
Popular Examples of Two Factor Authentication
Two-factor authentication (2FA) enhances security by requiring two forms of verification. Here are some popular examples that illustrate how 2FA works effectively.
SMS Verification
SMS verification sends a one-time code to your mobile device. You enter this code after logging in with your password. Many services, like Google and Facebook, use this method. While convenient, it’s essential to recognize that SMS can be vulnerable to interception. However, it’s still widely used for its simplicity and accessibility.
Authenticator Apps
Authenticator apps generate time-based one-time passwords (TOTPs). Applications like Google Authenticator and Authy provide secure codes that refresh every 30 seconds. This method offers better security than SMS since the codes are generated on your device without relying on an outside source. Plus, these apps often work offline, ensuring access even without internet connectivity.
Biometric Authentication
Biometric authentication uses unique physical characteristics for verification. Examples include fingerprint scans and facial recognition found in devices like smartphones and laptops. This approach adds a personal touch to security; you can’t replicate your fingerprint or face easily. Consequently, many banking apps utilize biometric methods for added protection against unauthorized access.
By understanding these examples of two-factor authentication, you can make informed choices about securing your accounts more effectively.
Benefits of Using Two Factor Authentication
Implementing two-factor authentication (2FA) provides significant advantages in securing your online accounts. It not only enhances security but also builds user trust and confidence.
Enhanced Security
Enhanced security is the primary benefit of using two-factor authentication. By requiring a second verification step, you significantly reduce the risk of unauthorized access. For instance, even if someone steals your password, they can’t log in without the second factor. Common methods include:
- SMS Verification: A one-time code sent to your mobile device.
- Authenticator Apps: Generate time-based codes on your smartphone.
- Biometric Authentication: Uses fingerprints or facial recognition.
These methods create barriers that protect sensitive information from cyber threats.
User Trust and Confidence
User trust and confidence increase with two-factor authentication. When you know that an extra layer of security is in place, it reassures you about protecting personal data. Many users feel more secure knowing their accounts are safeguarded against breaches. Companies that implement 2FA often see improved customer loyalty as clients appreciate proactive measures for safety. Wouldn’t you prefer services that prioritize your security?
Implementing Two Factor Authentication
Implementing two-factor authentication (2FA) significantly strengthens your account security. It adds an essential layer of verification, reducing the risk of unauthorized access. Understanding how to set it up effectively can make a notable difference.
Best Practices for Setup
- Choose Strong Authentication Methods: Opt for methods like authenticator apps or hardware tokens over SMS. These options provide better security against interception.
- Enable 2FA on All Accounts: Activate 2FA across all critical accounts, including email, banking, and social media. This uniformity helps maintain robust protection.
- Backup Codes Are Crucial: When setting up 2FA, generate backup codes. Store them securely in case you lose access to your primary method.
- Educate Users: If you’re managing multiple accounts or overseeing others, ensure everyone understands how 2FA works. Knowledge reduces mistakes during login attempts.
- Neglecting Backups: Forgetting to keep backup codes can lock you out of your account if the primary method fails. Always have alternatives ready.
- Using Weak Passwords: Even with 2FA, weak passwords compromise security. Combine strong passwords with 2FA for optimal protection.
- Ignoring Security Updates: Failing to update your authenticator app or device can expose vulnerabilities. Regular updates help maintain security integrity.
You’ll notice that following these practices mitigates risks and enhances overall online safety. Prioritizing effective implementation ensures that your digital identity remains secure against potential threats.