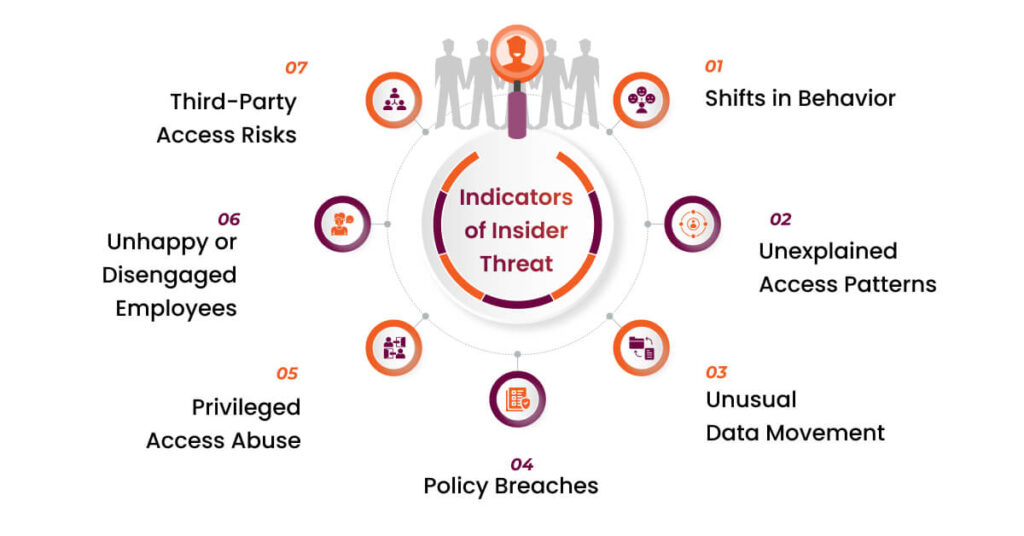
In today’s digital landscape, the risk of insider threats looms larger than ever. Potential indicators of insider threat can include behaviors such as unusual work patterns and sudden changes in attitude. Have you ever noticed a colleague acting differently or accessing sensitive information without reason? These subtle shifts might be more than just personal issues; they could signal deeper concerns.
Understanding these behaviors is crucial for safeguarding your organization. By recognizing potential warning signs early on, you can help prevent data breaches and protect valuable assets. This article will explore various examples of these indicators, providing insights into what to look for and how to respond effectively. Stay tuned as we delve into the world of insider threats and empower yourself with knowledge that could make all the difference.
Understanding Insider Threats
Recognizing insider threats involves observing specific behaviors. Potential indicators of insider threat can include behaviors such as:
- Unusual work patterns: For example, an employee might start working late hours or accessing systems outside their typical schedule.
- Sudden changes in attitude: If a team member becomes uncharacteristically withdrawn or irritable, it could signal underlying issues.
- Increased security breaches: Frequent attempts to bypass security protocols or access restricted data often indicate malicious intent.
Additionally, consider the following signs:
- Excessive sharing of sensitive information: Employees discussing confidential details publicly may pose risks.
- Frequent complaints about management or coworkers: Negative attitudes can escalate and lead to harmful actions within the organization.
Stay vigilant and monitor these behaviors closely. Identifying early warning signs plays a crucial role in safeguarding your organization against potential insider threats.
Behavioral Indicators of Insider Threats
Recognizing behavioral indicators can help you identify potential insider threats early. Certain actions and changes in demeanor may signal risks that require immediate attention.
Unusual Work Patterns
Employees exhibiting Unusual Work Patterns might raise red flags. Here are some examples to consider:
- Working late hours consistently, especially without a valid reason.
- Accessing sensitive data during odd hours, outside typical business times.
- Frequent absences or sudden requests for leave without clear explanations.
These behaviors can indicate someone is attempting to conceal activities or access information they shouldn’t.
Sudden Changes in Attitude
Changes in an employee’s attitude often serve as strong warning signs. Look for these specific behaviors:
- Becoming withdrawn from colleagues and avoiding team interactions.
- Exhibiting irritability, such as expressing frustration over minor issues.
- Increasing complaints about management, reflecting dissatisfaction that could lead to malicious intent.
Noticing these shifts can be crucial in addressing potential threats before they escalate.
Access and Usage Indicators
Access and usage indicators highlight behaviors that may suggest insider threats. Recognizing these signs early enhances your organization’s security posture.
Unauthorized Access Attempts
Unauthorized access attempts often raise alarms. For instance, if you notice repeated failed login attempts to sensitive systems, this behavior could indicate malicious intent. Additionally, accessing data outside of normal business hours or from unusual locations signals potential issues. You should track:
- Login failures: Multiple unsuccessful tries can hint at hacking efforts.
- Access from strange devices: Using unrecognized hardware might mean someone’s trying to bypass security measures.
- Frequent logins: If an employee accesses systems excessively without a clear reason, it’s worth investigating.
Excessive Data Downloads
Excessive data downloads serve as another red flag. When employees download large amounts of sensitive information without justification, it raises suspicion about their motives. Consider monitoring the following:
- High-volume downloads: Unexplained bulk data transfers should trigger scrutiny.
- Patterns in downloads: Look for repeated access to confidential files over short periods.
- Data types: Focus on critical or proprietary information; unauthorized handling can lead to serious breaches.
By keeping an eye on these access and usage indicators, you can better protect your organization against potential insider threats.
Social Interactions and Relationships
Social interactions and relationships within an organization can reveal significant indicators of potential insider threats. Changes in how employees engage with their colleagues often signal underlying issues.
Changes in Relationships with Colleagues
Changes in relationships often manifest when an employee becomes less communicative or isolates themselves from team members. For example, you might notice someone who previously collaborated well now avoids conversations or group activities. Additionally, if they express distrust towards coworkers or stop participating in team meetings, these behaviors raise red flags. Disengagement from social circles can indicate personal turmoil or a shift toward negative intentions.
Expressing Discontent with Policies
Expressing discontent with organizational policies can also serve as a warning sign. If you hear an employee openly criticize company procedures, especially those related to security measures, it suggests potential dissent. Frequent complaints about management decisions, particularly concerning data access protocols, may indicate frustration that could lead to harmful actions. Monitoring these discussions is crucial; they can highlight vulnerabilities before they escalate into serious threats.