In a world overflowing with information, how can you harness the power of publicly available data? Open Source Intelligence (OSINT) examples offer a treasure trove of insights that can transform your approach to research and security. From uncovering hidden connections in social networks to analyzing satellite imagery, OSINT techniques empower you to make informed decisions.
What Is OSINT?
Open Source Intelligence (OSINT) refers to collecting and analyzing information from publicly available sources. You can find these sources in various formats, including websites, social media platforms, news articles, and government reports. OSINT enables individuals and organizations to gather valuable insights without needing proprietary or classified data.
Examples of OSINT include:
- Social Media Analysis: By examining public profiles on platforms like Twitter or Facebook, you can uncover trends or sentiments related to specific topics.
- Geospatial Data: Tools like Google Earth let you analyze satellite imagery for changes in infrastructure or land use.
- Public Records Search: Accessing government databases provides information about business licenses, property ownership, and legal filings.
OSINT plays a crucial role in security assessments and strategic planning. With it, you can make informed decisions based on comprehensive data analysis. Are you leveraging these resources effectively?
Importance Of OSINT
Open Source Intelligence (OSINT) plays a pivotal role in gathering and analyzing publicly available information. Its significance lies in its ability to enhance security, support investigations, and facilitate informed decision-making.
Enhancing Security
OSINT strengthens security measures by providing crucial insights. For instance, organizations can monitor social media platforms for potential threats or anomalies. By analyzing posts related to their brand or industry, they can identify emerging risks early on. Moreover, tracking discussions on forums helps detect malicious activities targeting specific entities. Utilizing geospatial data from satellite imagery also aids in assessing vulnerabilities of physical locations.
Supporting Investigations
OSINT acts as a valuable tool for investigators across various fields. Law enforcement agencies often utilize public records to gather information on suspects. This includes searching property ownership records or business licenses that reveal connections between individuals and organizations. Additionally, journalists leverage OSINT techniques like verifying sources through social media profiles or news articles to ensure accuracy in reporting. In cybersecurity, analysts analyze domain registrations and IP addresses to trace cybercriminals effectively.
Incorporating OSINT into your security protocols and investigative practices enhances overall effectiveness while utilizing available resources efficiently.
OSINT Examples In Different Sectors
OSINT finds applications across various sectors, showcasing its versatility. Here are some key examples.
Government and Law Enforcement
Government agencies utilize OSINT to enhance national security. They analyze social media posts for potential threats and track online activities of individuals involved in criminal networks. For instance, law enforcement can gather intelligence on drug trafficking by monitoring discussions in specific forums. Additionally, public records searches aid investigations into suspicious activities or individuals.
Business and Competitive Intelligence
Businesses leverage OSINT to gain insights into competitors and market trends. By analyzing news articles, press releases, and social media activity, companies can identify customer sentiment and emerging patterns. For example, a tech firm may monitor competitor product launches through online reviews and feedback on platforms like Twitter. This information helps businesses make data-driven decisions regarding marketing strategies and product development.
Cybersecurity
Cybersecurity professionals use OSINT to identify vulnerabilities. They scan the web for exposed databases or leaked credentials that could pose risks to their organizations. Tools such as Shodan allow experts to find unsecured devices connected to the internet. Furthermore, threat intelligence reports rely on publicly available data about malware outbreaks or phishing attempts to bolster defenses against cyber attacks.
Journalism and Investigative Reporting
Journalists employ OSINT techniques for fact-checking and source verification. They access official documents, social media profiles, and user-generated content to corroborate stories or uncover new angles. For instance, investigative reporters might analyze satellite imagery using tools like Google Earth to verify claims made by sources about environmental changes or illicit activities. This approach enhances credibility and provides a more comprehensive narrative.
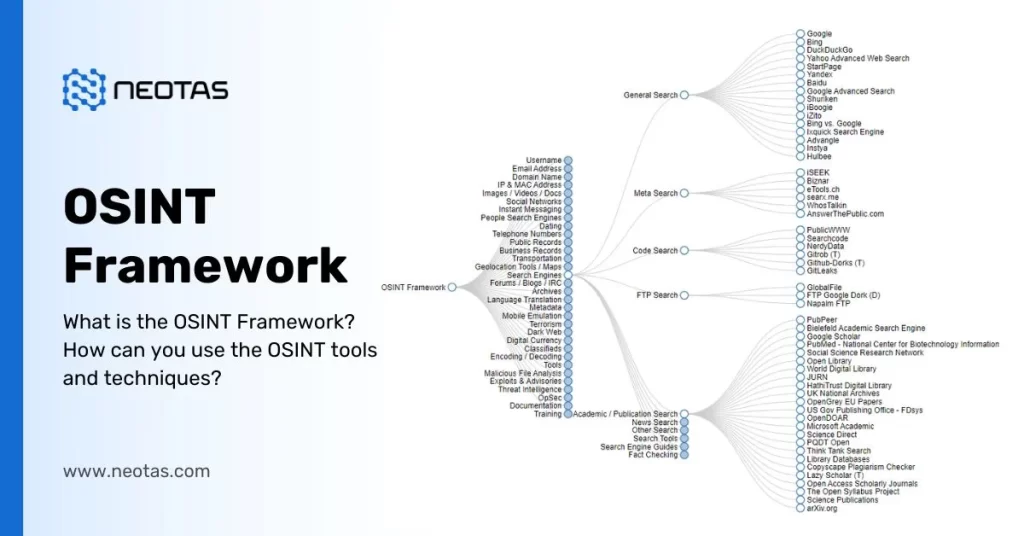
Tools And Techniques For OSINT
OSINT relies on various tools and techniques that enhance data collection and analysis. These resources help you gather information effectively, transforming publicly available data into actionable insights.
Data Collection Tools
Data collection is essential for OSINT. Numerous tools facilitate this process:
- Maltego: This tool helps visualize relationships between people, organizations, and online accounts.
- Shodan: It enables the search of devices connected to the internet, uncovering vulnerabilities.
- Google Dorks: You can use specialized queries in Google to find specific types of data across websites.
- Social Media Scrapers: These tools extract data from social media platforms like Twitter or Facebook for trend analysis.
These options allow you to gather diverse datasets from multiple sources quickly.
Analysis and Visualization Tools
Once collected, analyzing and visualizing the data becomes crucial. Several tools stand out:
- Tableau: This software transforms complex datasets into interactive visualizations.
- Gephi: Ideal for network analysis, it helps map connections within large datasets visually.
- IBM i2 Analyst’s Notebook: It assists in identifying patterns through link analysis across different types of information.
- ArcGIS Online: Use this platform for geospatial analysis to understand geographical trends better.
These analytical tools turn raw data into understandable formats, making it easier to draw conclusions and make informed decisions.
Challenges In Implementing OSINT
Implementing Open Source Intelligence (OSINT) presents several challenges that organizations must navigate. Understanding these obstacles can enhance the effectiveness of OSINT strategies.
Legal and Ethical Considerations
Legal frameworks governing data collection can complicate OSINT efforts. Organizations must comply with laws regulating privacy and data protection, such as GDPR in Europe or CCPA in California. Violating these regulations can result in severe penalties. Additionally, ethical dilemmas arise when determining the appropriateness of certain information collection methods. For example:
- Public vs. private: Distinguishing between publicly available information and what infringes on personal privacy is crucial.
- Intent of use: Considering how collected data will be used impacts ethical considerations.
You must establish clear guidelines to balance effective intelligence gathering with compliance and ethics.
Data Overload Issues
The sheer volume of available data poses another significant challenge for OSINT practitioners. Filtering through vast amounts of information can lead to analysis paralysis if not managed effectively. Here are some common issues:
- Relevance: Identifying which data points are pertinent often becomes overwhelming.
- Quality control: Ensuring the accuracy and reliability of sources is vital; misinformation can mislead decision-making processes.
To combat data overload, employing automated tools for sorting and prioritizing information helps streamline the analysis process while maintaining focus on key insights.